7 cybersecurity priorities for government agencies and political campaigns
As we approach November, the digital election infrastructure finds itself in the crosshairs of a new peril. Authoritarian forces and other adversaries have weaponized the fifth domain of warfare — cyberspace — against the very fabric of democracy. As the election process ramps up, organizations engaged in the political process must strengthen cybersecurity to prevent chaos and disorder from carrying the day. In so doing, they face unprecedented challenges.
Nation-state attackers and unscrupulous internal forces threaten the integrity of the electrical process, the faith of the voters in the best form of government yet devised by mankind, and even the sense of fraternity or unity among the people themselves. Cybercriminals — having already pivoted to take advantage of confusion and disruption from the pandemic — are now poised to exploit yet more opportunities.
We’ve had many warning signs in the form of the bots and trolls disseminating fake news in 2016 along with the breach of the Democratic National Committee email system. More recently, we’ve seen activists using the TikTok service to disrupted a Trump campaign rally, hackers compromise Joe Biden’s and other celebrities’ Twitter accounts, and phishing attempts against state-level voter registration system personnel.
Campaigns, Government Agencies, and Election Vendors in the Crosshairs
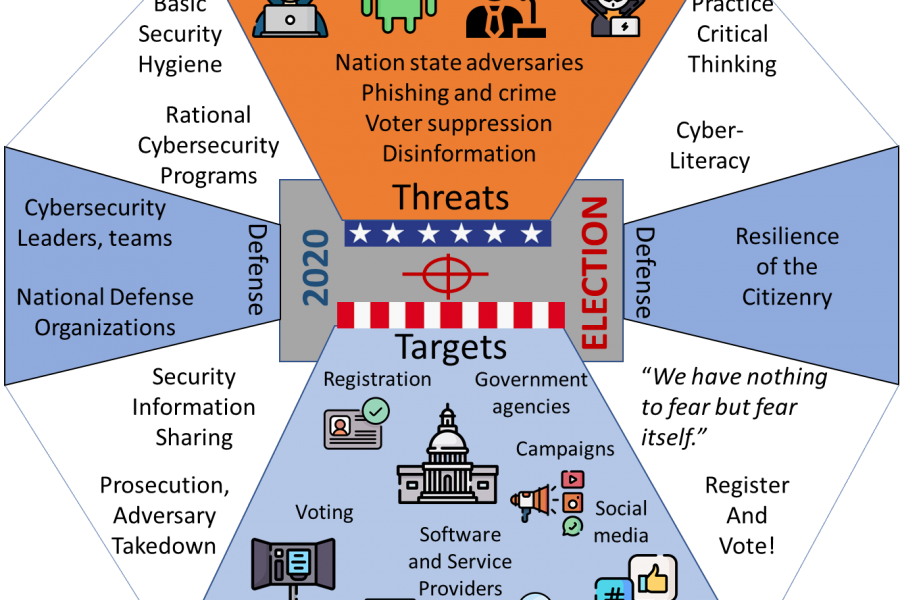
Although we’re far from full online voting, many other aspects of the political process are going digital. A bewildering number of organizations are getting information out to voters, campaigning for votes, managing the election process and collecting or counting results. As a result, the two key questions we now have to ask ourselves are: What are we trying to protect in the election process, and what is the “critical infrastructure” for an election? Per Figure 1 (above), here are the players in the digital election infrastructure:
- National or state-level government agencies that manage registration, voting, and all other election processes
- Campaign organizations or political action committees through which people and businesses contend for their political agendas
- Media and social media through which campaign organizations influence voter opinion and citizens gather or share information
- Companies providing software or services (such as registration databases, call centers, websites, and applications) to such agencies, campaigns, and media organizations
Each of these organization types requires a security program. During COVID-19 lockdowns, reopenings and second waves, all have faced accelerated digital transformation. During crises, IT and security teams tend to cut corners. For example, the so-called Twitter cryptocurrency hack may have been facilitated by a work-from-home program that weakened administrative account recovery controls.
Now that the excitement of the political season begins, it may feel like accountability for security is suspended. But that is a dangerous illusion that could be spectacularly shattered in the next breach, and we cannot afford more serious breaches against democracy itself.
To read the complete article, visit Dark Reading.