Advances in location analytics fuel law-enforcement applications
What is in this article?
Advances in location analytics fuel law-enforcement applications
Analytics have been used by law-enforcement agencies for decades, but gained wider acceptance among large urban police departments in the 1990s, when the controversial “Broken Windows” theory—cracking down on seemingly minor crimes, such as graffiti and broken windows, to signal that more serious crimes would not be tolerated—was used to introduce crime mapping and pattern analysis. This resulted in the lowest crime rates in a generation in New York, Los Angeles, and other cities.
Similarly, clandestine federal government agencies have been using analytics against foreign surveillance targets for years. More recently, the government has relaxed restrictions on how federal agencies are able to search, retrieve, and store data gathered by such agencies for purposes other than national security threats. Private information on U.S. citizens—e.g., credit card data and travel records—now will be stored for five years, and these databases will be subject to data mining – the use of complex algorithms to search for patterns that predict a threat.
The reported driver for this policy change was the failure by intelligence agencies to connect the dots about the so-called “underwear bomber,” who was convicted of trying to detonate plastic explosives, which he had hidden in his under garments, on a Northwest Airlines flight between Amsterdam and Detroit on Christmas Day in 2009. This failure was despite intelligence agencies having intercepted mobile phone communications and field reports related to the attacker prior to the incident.
With this renewed focus on analytics, law-enforcement agencies have an expanded toolbox with which to fight—and often prevent—crime.
Connecting the dots
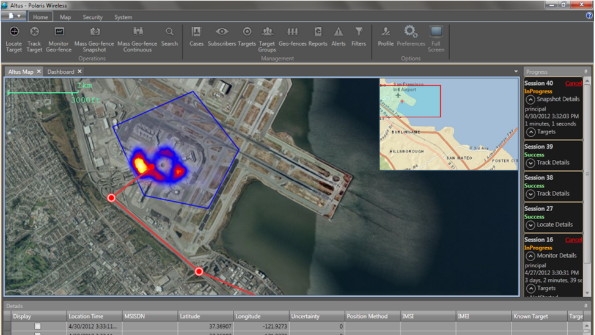
Arguably the most powerful capability that law enforcement agencies can possess is predictive analytics. With this in place, they can identify behavior patterns of known criminals and selectively deploy resources to prevent attacks. By monitoring the location of suspects over a period of time, the security agencies are able to create “heat maps” that identify areas of consistent activity. These are then used by the agencies to assign priority to areas for increased monitoring and to optimally deploy personnel and equipment.
Law-enforcement agencies now can predict the location of suspected criminals based on their observed activities during a given time of day, and work to head them off before they attempt an attack. Using high-accuracy location, the security agencies also have gained the ability to track targets. The locations of tracked targets are then compared against existing security databases to further identify suspicious activity and select suspects for increased surveillance or other preventive actions.
In some jurisdictions, laws enable surveillance of all targets in a given area for the purposes of fighting crime. One standards-based, high-accuracy location solution, RF Pattern Matching (RFPM), uniquely supports mass location surveillance of all subscribers on a wireless network. This capability enables the identification of all subscribers in a defined geographic area and is vital to the monitoring of sensitive or highly vulnerable areas within the country.
For example, law-enforcement agencies are now able to deploy a geo-fence around a known gang headquarters to alert them when any identified targets approach. This greatly enhances the level of security, and enables law enforcement to identify who was in and around an area in the time before and after an incident. This list then can be compared against known gang members to confirm the suspects and augment any subsequent investigation.
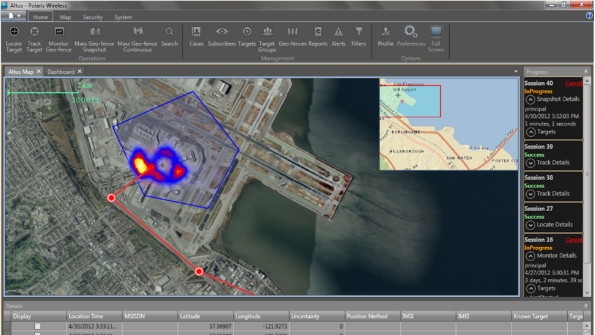
Figure: Geo-fence with heat map
Source: Polaris Wireless
RFPM is a network-based positioning method that is based on radio link measurements collected from the network and/or the device. It relies on predictions or models of the radio environment against which it performs an algorithmic comparison of the measurements, in order to determine a best-match estimation of the device location. In short, it uses the device’s own radio signals to identify its location, eliminating any dependency on satellites or other network hardware.
RFPM is able to locate all devices across any air interface and in any environment, eliminating limitations related to the device type or network technology. In addition, it works extremely well in non line-of-sight conditions such as dense urban and indoor environments, and is highly reliable for mission-critical public-safety applications.