Arresting developments
When a convicted criminal is sentenced to prison, the natural instinct for involved parties — particularly victims, witnesses and attorneys — is to breathe a sigh of relief that the matter is behind them and that the criminal will not bother them during his or her incarceration.
But that is not always the case today. Although prisoners are not allowed to have cell phones, inmates using contraband device are using wireless technology as a tool to communicate with those outside the walls of correctional facilities — without the nuisances and limitations associated with conversations conducted on a prison landline phone that is monitored at all times.
“What this has done is just basically torn down the prison fence,” said Josh Gelinas, communications director for the South Carolina Department of Corrections. “Once you have a cell phone, you have access to everything. With cell phones and e-mail access, they are basically able to continue their criminal enterprises behind prison bars — in some cases, with the same efficiency as they could if they were not in prison.”
Some of the more high-profile examples of the problem include Patrick Byers, who used a cell phone while in a Baltimore city jail to order the 2007 murder of witness Carl Lackl. In 2008, Texas death-row inmate Richard Tabler threatened the life of Texas state senator John Whitmire using a cell phone smuggled to him by a prison guard who was paid by Tabler’s family.
In March of this year, Capt. Robert Johnson — a “contraband captain” at Lee Correctional Institute in Bishopville, S.C., tasked to stem the tide of cell phones and other illegal items reaching inmates — was shot in his home six times. While the investigation is not complete, “we know the hit was put out by an inmate inside Lee Correctional facility and that someone shot [Johnson],” Gelinas said.

Johnson’s shooting was especially troublesome to the South Carolina corrections system because its officials two years earlier had seen a demonstration of an RF jamming solution they believed would effectively put a halt to inmates communicating wirelessly beyond prison walls, without harming prison staffers’ land-mobile radio signals or legitimate commercial calls outside the facility.
However, current law prohibits state and local agencies from installing jamming equipment of any kind, and the debate whether such technology should be allowed has become a hot topic in the wireless industry, which has offered technologies such as detection, managed access and controller systems as potential solutions.
As policy-makers and the wireless industry continue to debate the issue, the dangers associated with the contraband cell phones remain very real, Gelinas said.
“There is blood on the ground,” he said. “Had jammers been in place at Lee Correctional Institute, that call would not have gone out and that hit would not have been carried out. Unfortunately, it looks as if it’s going to take more dead bodies before the FCC and Congress are going to take action and give prisons the power they need to solve the problem.”
How did the phones get in there?
While opinions differ on the best way to resolve the issue of contraband cell phones in prisons and jails, there is agreement that the matter needs to be addressed quickly. Although cell phones are illegal for inmates to have — in fact, in many prison systems such as South Carolina, even prison personnel are not allowed to use them within a correctional facility — the devices continue to end up in the hands of incarcerated criminals at an alarming rate.
Officials in the states of California and Maryland have reported that the number of cell phones confiscated in prisons increased 70% last year. In South Carolina, Gelinas said that 3,024 cell phones and components were found in its 24,000-inmate prison system during the last fiscal year — a 41% increase compared to the prior year.
And those numbers reflect only the cell-phone devices that have been confiscated; the actual number of contraband wireless devices used in correctional facilities likely is higher. Indeed, CellAntenna CEO Howard Melamed said that his company’s detection technology revealed 239 cell phones being used in a 400-inmate wing of a Texas correctional facility.
Given that inmates are prohibited from having cell phones in prisons, the revelation of such statistics typically is followed by questions about why security measures such as metal detectors, trained dogs and human searches have been unable to curb the problem.
In some cases, the security measures themselves may be lax, or they aren’t being executed effectively to prevent the introduction of cell phones into correctional facilities. But sources interviewed for this story also noted the sometimes-extraordinary resourcefulness of inmates to devise methods to sneak contraband into their cells. With almost endless time on their hands, inmates plot to transport cell-phone components into prison via methods as seemingly extreme as ingestion and excretion.
In addition, inmates with accomplices outside the prison are much more difficult to stop, with one popular method of delivery being the insertion of cell-phone components — which are shrinking with each generation of devices — into Nerf balls that can be launched over the walls of corrections facilities.
“[Contraband] stopped coming through the front door with visitors and corrupted staff and started coming over the fence line,” Gelinas said.
Regardless of the method used to secure a cell phone, the effort is worthwhile to the perpetrator. Inside prison walls, cell phones are the top contraband item among inmates, Gelinas said. Amit Malhotra, Tecore Networks’ vice president of marketing, echoed this sentiment.
“The going rate that I’ve heard of for a cell phone is between $2,500 and $4,000,” Malhotra said. “I heard a prison official say that this is more valuable than narcotics, in certain instances. If you think about what they are able to achieve once they get a cell phone, it is very valuable to them.”
With such a high demand, the idea of becoming a supplier can be tempting — too tempting for some guards and other correctional personnel who can double their salaries by selling two $30 prepaid cell phones monthly to inmates.
“I hire from the human race, so they do make mistakes,” said Joseph Higgs, superintendent for the Rappahannock Regional Jail in Stafford, Va. “I’ve had security officers that have gone bad, and we’ve had to terminate them for giving a cell phone to an inmate or trying to assist an inmate with a personal problem. We tell our staff, ‘These people are not your friends.’ But you live with them, you eat with them and you’re around them 24/7, and you sometimes forget that.”
Potential solutions
Most agree that traditional security measures are not effective enough to resolve the issue of contraband cell phones in correctional facilities. However, technologies that detect device usage and even provide location information for the caller have gained some traction.
CellAntenna offers a detection service that can help correctional facilities identify and confiscate cell phones over a several-day period, which could serve to discourage — or at least delay — the use of the devices by inmates, Melamed said. For entities that lack the money to pay for a permanent system, regular use of such a service can help curb the problem.
But detection systems have drawbacks. First, detecting that a phone has been used does not prevent a call from being made. Second, after a phone has been detected, prison resources must be used to find and confiscate the device, something budget-strapped correctional facilities would rather avoid.
In addition, while a phone often can be found, it is much easier for an inmate to hide the tiny SIM card (see photo on previous page) that contains subscriber plans and contact information. Inmates with SIM cards will view the loss of a phone as only a temporary setback, Malhotra said.
“As long as they can find another phone, they are back in business,” he said.
With this in mind, Tecore Networks has developed a managed-access solution called the intelligent network access controller (iNAC) that resides on the carriers’ networks. Authorized users are able to make calls from inside a correctional facility, but the carriers do not allow any other cell-phone transmissions through their networks. Malhotra said. Tecore’s iNAC has gained the support of many commercial carriers, whose cooperation is integral to any solution, largely because its deployment would not require a change to existing law.
“Managed access is the optimal solution, because it gives the corrections administrators what they want, which is the ability to immediately prevent contraband cell phones from communicating while still being legal and allowing authorized and necessary communications — [including] emergency communications — all while being available today,” he said.
CellAntenna offers a similar controller-driven solution with one key difference: instead of the authorizing decisions being made within the carrier networks, it is done with equipment housed and maintained by the corrections facility, Melamed said.
CellAntenna believes its controller solution will require less equipment than Tecore’s iNAC and, therefore, should be less expensive, Melamed said. More importantly, the CellAntenna controller solution keeps the commercial wireless carrier out of the loop, simplifying the process and making the system more secure by reducing the number of people with authorization privileges.
While U.S. carriers seem to favor the Tecore approach, Melamed said carriers in other parts of the world like the CellAntenna controller solution, because they cannot be held responsible for unauthorized calls being made.
“[Foreign wireless carriers] look at it as more of a liability,” he said. “If they don’t turn off that guy who ends up killing somebody by calling on a cell phone and ordering a hit, then the liability is pretty high. [In the U.S.], they haven’t even thought of those issues.”
But the most-debated technology being considered is RF jamming — an interfering signal designed to block a cell-phone call. Cell-phone carriers, public-safety organizations such as the Association of Public-Safety Communications Officials (APCO) and prison officials such as Higgs have submitted filings opposing such an approach, stating that jamming is illegal and that the technology could generate interference that would hamper legitimate commercial and public-safety wireless communications, including areas that were not supposed to be subject to jamming.
“We just don’t believe that jamming or detection will solve the problem,” Tecore’s Malhotra said. “First of all, there’s tremendous uncertainty about how effective it’s going to be in the prison. It’s never been deployed across an entire prison facility.”
That may be the case in the U.S., but CellAntenna has deployed numerous jamming solutions in correctional facilities in other countries, Melamed said. CellAntenna not only can limit the jamming signal to a specified geographic area, it is sensitive enough to jam cell signals operating at 800 MHz without impacting prison personnel’s LMR communications operating on interleaved channels in the same band, he said.
An outspoken opponent of indiscriminate jamming, Melamed said the important thing is that any enabling jamming policy or legislation be written to hold engineering groups accountable for unwanted interference, so the jamming solutions are properly designed and installed.
“If it’s done right, you’re not affecting anybody,” he said. “If it’s not done right, you’re affecting everybody. So do it right.”
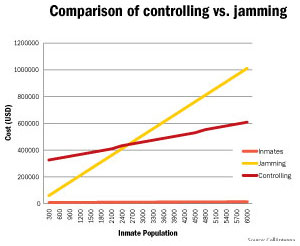
And, depending on the size of the correctional facility, jamming is the most cost-effective solution, as well, Melamed said.
Gelinas is convinced, noting that South Carolina’s demonstration of the Cell Antenna technology revealed that cell-phone communications were blocked without impacting LMR communications. Upon taking one step out of the room where jamming was deployed, attendees were able to make cell-phone calls again, he said.
“We believe jamming is the best solution for not only our prison system but for other prison systems, as well,” Gelinas said.
Decision time
Contraband cell-phone use in prisons has been getting attention in Washington, D.C. Last year, the U.S. Senate passed legislation that would legalize jamming in correctional facilities. However, the bill is not getting much traction in the U.S. House, which has passed a separate measure that makes it a felony for an inmate to use or possess a cell phone. The House bill also includes penalties for those providing an inmate with a cell phone.
Meanwhile, the National Telecommunications and Information Administration (NTIA) recently conducted a proceeding to solicit comments from interested parties on the matter.
Gelinas said he hopes federal lawmakers and policy-makers are able to set a direction on the matter soon, because the South Carolina corrections department has wanted to address a technological for a couple of years but has been hampered by existing laws. After the shooting of Johnson, Gelinas believes that federal officials now should have all the incentives they need to move quickly, but is admittedly skeptical.
“Here, we [the South Carolina corrections department] are yelling as loud as we can for help, and one of our guys goes down in a shooting,” he said. “I think, in the big picture, people don’t fully grasp what’s happening. Unfortunately, it’s probably going to stay that way until somebody high profile gets hurt.”
















