What could have been done?
The main idea to be relayed through this hypothetical scenario is that today’s cyber-attacks do not typically show obvious attack indicators until it is too late.
But there were in fact several indicators along the way in this scenario. During the first wave of attacks, i.e., the spear-phishing at the Sheriff’s Office, the attack was detected and stymied. The Sheriff’s Office, after identifying an attack, should have alerted the other agencies and submitted the attachment to their anti-malware vendor for analysis. At the least, this could have added some new data for signatures used in intrusion-detection systems. But the “instant interagency cooperation and information sharing” that the mayor spoke of was nonexistent, because a “silo culture” still exists in the public-safety sector.
Cyber-warfare has long been described as a game of cat and mouse. The attackers create something new, a signature to detect and stymie is developed, and then the attackers adjust by slightly modifying the attack method. It is exceedingly difficult to stay ahead of the game, but numerous tools exist that would have been helpful in this scenario.
For instance, the second wave of attacks targeted the surrounding agencies with a new change to the malware, which allowed it to get past the local anti-virus and intrusion-detection signatures. There are several tools on the market known as indicators of compromise (IOC) that are supported by the open-source community. They are continually updated as new threats occur. Any of the agencies could have used an IOC to scan their systems.
An IOC focused on the family of RATs that was installed would have triggered, at a minimum, a higher risk alert, such as those depicted in Figure 2. This would have enabled security administrators—who typically take a holistic approach to security—to concentrate their efforts on specific machines. The last indicator of this wave of the APT was the traffic leaving the agency to the command-and-control server; it is highly possible it would have gone undetected throughout the entire staging process.
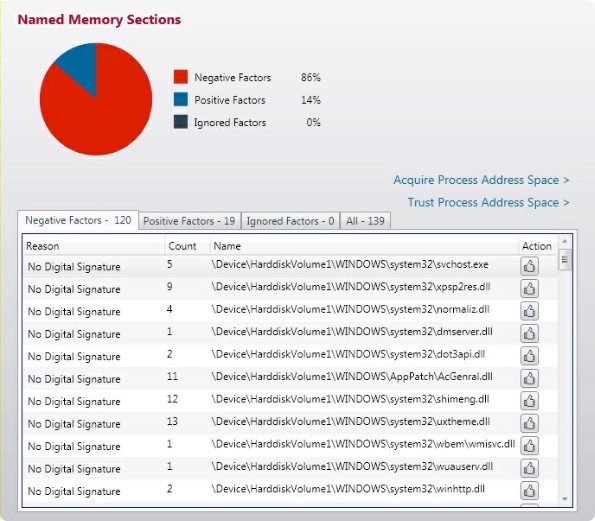
Figure 2–Attack indicators
Source: Mandiant Corp.
The next wave of the APT modified the GIS boundaries. This also could have been mitigated. Attackers used the vendor’s documentation to make the necessary changes to this seemingly benign area, undetected. Having worked for more than 15 years exclusively protecting 911 systems, the importance of guarding against unverified changes to GIS datasets is obvious to this writer.
An additional layer of protection for this scenario would be to consolidate GIS updates to a single person or group. All requested updates or changes made by local GIS teams would be submitted to a 911 GIS administrator for a scheduled and controlled update. Any changes to the GIS databases then should trigger, at a minimum, an event in the system logs that should be monitored.
Flooding the Sheriff’s Office CAD queues with automated calls is not normal. Perhaps in weather-related emergencies, such as a hurricane or tornado, or in socially driven ones like a riot, would the call volume spike the way it did on the day of the heist. This was a clear indication that something was wrong. Unfortunately, it’s never immediately clear whether there was criminal intent.
In this case, by the time law enforcement could determine the calls flooding the CAD system were spurious, the Diamond Exchange heist was long over. Recall that these faux calls for service were generated from the agency zombies, which were inside and acting as an extension to the 911 service. At that time, agency personnel may have noticed a slow-down of their systems. This possibly was the only externally visible indicator seen by the agencies.
The last APT was the DDoS carried out by the external zombies, which generated a flood of calls into the Sheriff’s Office and 911 center, tying up their lines. Having had access to the system over several months, and the vendor’s documentation, it was not long before the attackers had the information they needed for a targeted DDoS attack against the center.













