Code of misconduct (with related video)
It’s almost impossible anymore to pick up a newspaper or weekly magazine without finding a headline or article about the latest virus or cyber attack resulting in stolen information or a shut-down of someone’s network. While in the past these attacks primarily have impacted or targeted Internet-connected machines or business enterprise networks and information systems, we now are seeing an alarming increase in reports of cyber attacks on the systems and networks supporting mission-critical communications in the government, public-safety and utility sectors.
This is occurring because the systems and equipment that were used in the past for communicating, call-taking and dispatching were relatively “unintelligent” — in other words, there wasn’t much to attack. For example, 911 systems and associated customer premise equipment, or CPE, depended on direct lines to the central office and circuit-switched hardware. Legacy conventional radio systems also were primarily hardware based, and as such offered little opportunity for an attack point.
Connecting to these systems from the dispatch center most often relied on dedicated leased lines or point-to-point microwave links. And of course, in most cases each of these subsystems operated independently of the other — that is, there was no end-to-end transfer of data or information other than that done by the dispatcher.
However, today’s mission-critical communications environment — radio systems included — leverage the same IP platforms and operating systems as any other IT network. IP, while an enabling technology, also introduces the same risks and vulnerabilities regarding cyber attacks as any IT network. Exposure to viruses, denial-of-service attacks, hardware and software failures, intrusions by malicious hackers, data loss, and system downtime all are potential risks that should be keeping managers and operators of these critical networks up at night.
For purposes of discussing potential threats and vulnerabilities, and approaches to mitigating them, we’ll examine the three major elements of the mission-critical communications environment:
Connectivity network and backbone. IP networks are a key enabling element of all modern communications including mission-critical public-safety and utility dispatch and monitoring systems. In the public-safety environment, ESInets supporting next-generation 911 rely on the same IP network technology, and thus have the same potential vulnerabilities.
Automated systems and applications. This element includes critical systems such as CAD/RMS, telephone CPE, monitoring and control (e.g. SCADA), mapping/GIS, and so on. Most of these mission-critical specific applications and tools are built on the same operating systems and architectures as other modern enterprise network systems – and are susceptible to the same kinds of cyber attacks.
Radio and wireless systems. Modern land-mobile voice and data systems (such as trunked systems and wireless data networks) also are architected using the same server and IP network connectivity as modern enterprise network systems — and again bring similar vulnerabilities. Plus, the wireless environment adds a layer of unique security challenges.
In addition to the potential individual vulnerabilities that each of these respective subsystems carries, the current trends toward convergence and connectivity of these elements requires that a holistic approach to cybersecurity must be employed in order to “close all the doors.” That is, as these pieces are connected in order to efficiently pass information in an end-to-end environment, it’s not enough to protect any one or two elements — organizations must address and plan to protect all of them, including the network itself.
None of this is at all intended to suggest that implementing modern systems and tools, or converging these systems into a cohesive efficient network, is a bad thing. The benefits, capabilities and efficiencies of today’s mission-critical and public-safety communications systems and applications far outweigh any potential negatives. Our goal in this and following articles is to make you aware of the cybersecurity vulnerabilities and need to address them. Once aware, we hope to provide sound advice on assessing and mitigating these risks and vulnerabilities.
There is a constant barrage of activity that could inflict cybersecurity issues upon your systems. Every environment contains vulnerabilities, threats and risks. A vulnerability is a condition or weakness in the operating environment that may require measures to prevent a security issue. It absolutely is critical that a public-safety agency understand the vulnerabilities it must address and the threats and risks it faces. A threat is the probability that a vulnerability will be exploited. A risk is identified as an opportunity to disrupt normal operations, i.e., the impact a threat will cause by exploiting a vulnerability. The general rule of thumb is that the greater the likelihood that a threat will exploit a vulnerability, the greater the risk to the operating environment.
In order to gauge the level of awareness regarding the need to address cybersecurity vulnerabilities, threats and risks in critical communications systems, L.R. Kimball, with the support of Urgent Communications, conducted a survey. It was focused on cybersecurity awareness in public-safety and critical radio communications systems. Some of the survey results illustrate the need for increased education and awareness of cyber-based vulnerabilities.
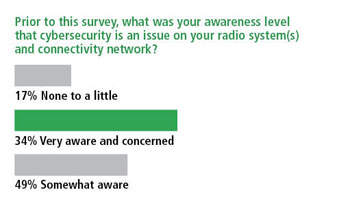
For example, only 34% of respondents were very aware that cybersecurity is an issue relevant to radio systems. At the same time, 26% of those responding indicate that they utilize an IP-enabled radio connectivity network for traffic other than radio, e.g., 911, computer-aided dispatch, and administrative communications, with an additional 24% planning for interconnection.
The responses to these two questions provoke several interesting discussion points. First, that only 34% of respondents indicated a full awareness that cybersecurity is a relevant concern for their radio communications system certainly confirms the need for education and increased awareness. Second, we found it interesting that 50% of the same respondent group already use, or are planning to use, their IP-enabled connectivity network to support both their radio system and other applications. This confirms the trend toward convergence mentioned previously, but to some extent we think it also confirms the lack of awareness of potential vulnerabilities brought to one system element (radio in this case) through convergence with another system element (the network and other applications being transported.)
 Other interesting awareness-related statistics from the survey are found in the responses to the question that asked whether the recipient’s organization currently has an information security officer in place. The good news is that 48% indicated that they do, and another 9% even indicated that they have someone in their radio or public-safety division responsible for information security. However, the bad news is that 43% indicated that their entity does not have anyone charged with this responsibility.
Other interesting awareness-related statistics from the survey are found in the responses to the question that asked whether the recipient’s organization currently has an information security officer in place. The good news is that 48% indicated that they do, and another 9% even indicated that they have someone in their radio or public-safety division responsible for information security. However, the bad news is that 43% indicated that their entity does not have anyone charged with this responsibility.
Given the apparent low awareness of the importance of cybersecurity in these systems, it is alarming that other responses confirm the growing trend of attacks and vulnerabilities in modern critical communications systems. For instance, nearly 12% of survey respondents indicated that their public-safety network or system has experienced a virus infection, while 9% indicated that an employee had damaged their computer system (intentionally or unintentionally).
The survey also asked respondents to rate various issues as hurdles to implementing cybersecurity within their organization. In particular, we were curious as to the impacts of budget on the ability to fund cybersecurity-related activities and, in a related question, asked them to indicate to what degree they felt other priorities might limit their attention on cybersecurity.
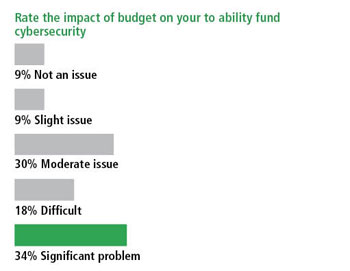
 More than half of the respondents indicated that budget issues were a significant or difficult impact on their ability to address cybersecurity. Interestingly, only 36% indicated that the many other needs facing their organizations made prioritizing cybersecurity a difficult or significant problem.
More than half of the respondents indicated that budget issues were a significant or difficult impact on their ability to address cybersecurity. Interestingly, only 36% indicated that the many other needs facing their organizations made prioritizing cybersecurity a difficult or significant problem.
In today’s economic climate it absolutely is essential that public-safety agencies spend their precious dollars wisely. This axiom applies to cybersecurity spending as well. But in many cases, we find that cybersecurity is not being included in capital or operational budgets. One factor, as mentioned above, is that awareness of the problem still is limited, despite strong evidence that indicates the number of cyber attacks on these systems is growing. Money is another factor. Even within entities that have recognized the need to address cybersecurity, more than half indicated that budgetary pressures make it difficult to fund such efforts. Moreover, about one-third of respondents indicated that other needs facing their organizations made prioritizing cyber security a difficult or significant problem.
In this first of a multipart series, we have outlined why this needs to change. Specifically, cybersecurity, as it relates to mission-critical and public-safety communications systems, is an issue that requires planning and action. One near-term action you might consider is reaching out to your organization’s in-house IT department. It is possible that you may be able to leverage the efforts of other tertiary departments in your organization to approach cybersecurity holistically.
Although mission-critical and public-safety communications systems have their own unique requirements and demands, the shared characteristics with enterprise networks and applications means that some of the same approaches to protection that your IT department already may be doing can be leveraged. A shared purchase may be able to distribute costs across multiple budgets, which in addition to cost savings may have the benefit of addressing your vulnerabilities, threats and risks from an even more holistic and inclusive vantage point. And, of course, don’t underestimate the value of outside assistance. Cybersecurity is a somewhat new topic for public-safety agencies and outside assistance can go a long ways toward ensuring you are implementing the right solution in the most cost-effective fashion.
 Now that we have increased your awareness of the need to address cybersecurity, we’ll move on to an overview of the vulnerabilities of each of the major subsystems, i.e., IP networks, automated systems and applications, and radio.
Now that we have increased your awareness of the need to address cybersecurity, we’ll move on to an overview of the vulnerabilities of each of the major subsystems, i.e., IP networks, automated systems and applications, and radio.
As this series continues, we will review the benefits of cybersecurity plans, policies, procedures and methodologies for maintaining a secure operating environment. We’ll also describe how to develop and apply sound strategies for keeping your mission-critical communications systems secure and resistant from this ever-increasing threat.
Lori J. Kleckner, PMP, CISSP is a cybersecurity consultant for L.R. Kimball with extensive experience in collaborating with agencies at the local, state and national levels. J. Kevin McGeary is a senior consultant in L.R. Kimball’s radio and wireless group with more than 35 years experience in public-safety communications. Jeremy L. Smith is an industry-recognized expert on securing public-safety systems. He holds CISSP and CISA certifications.