Why access control has become an important front in the war against cybercrime
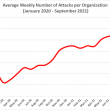
Earlier this year, Hiscox published its “Cyber Readiness Report 2021.” It was based on a survey of more than 6,000 companies based in the US, the UK, Spain, the Netherlands, Germany, France, Belgium, and Ireland. One of the most eye-catching findings was that spending per business on cybersecurity has more than doubled in the last two years.
However, this increased spending has been a rational response to the growing threat level. Based on Hiscox’s study, more firms were targeted by criminals in 2020 than in 2019, and 28% of businesses that suffered attacks were targeted on more than five occasions last year. Almost half of respondents said that they felt their organization had become more vulnerable to cyberattacks since the start of the pandemic, rising to 59% among businesses with more than 250 employees. Of those targeted, about one in six businesses said a cybersecurity event threatened the viability of their business. The survey also found that a payment had been demanded from around one in six of those hit by cyber criminals, with more than half paid.
Hiscox went on to assess firms’ maturity across six different areas of capability which comprise the elements required to install, run, manage, and govern an effective security system. One of those six areas was, “Identity and access management,” and, across all the companies surveyed, it came second bottom of the list.
Why Is Access Control an Important Part of a Cybersecurity Program?
The truth is that access control has not always been front of mind when it comes to cybersecurity, and many companies are still playing “catch up” in this area, but this is changing fast. More and more companies now appreciate that if access control systems are compromised, the daily operations of the building – and, consequently, its residents – could be at risk.
These companies are prioritizing measures to address the most urgent threats – five in particular:
- Man-in-the-middle attacks (MitM) – an attack where a hacker connects to a network and eavesdrops on communication between terminal devices. In this way, door opening codes and device login passwords can be hacked.
- Password/dictionary attacks – an attack where a hacker tries to guess the password to enter the device (normally using a password generator and trying different options).
- Unauthorized connection to a LAN network – the intercom or reader can be installed on the outside of the house and there is a potential risk that someone will break the intercom and use the UTP cable to connect to the LAN network.
- Unauthorized views of the intercom camera – it often happens that IP cameras are installed with a default password, and basically anyone can connect to it and watch what is happening.
- Malware attacks against mobile devices – mobile credential-based access control systems are increasingly popular, primarily because of the convenience they offer. However, they have also been a target for hackers, who have tried to attack smartphones with credential-theft, surveillance and malicious advertising.
To read the complete article, visit Dark Reading.