JPS enters cybersecurity space with IronGate solution to secure critical infrastructure
Historically known for its interoperability solutions, JPS today announced IronGate, the company’s first cybersecurity offering that is designed to prevent hackers from launching cyberattacks against the industrial-control systems that are crucial to the operations of critical infrastructure such as utilities and military facilities.
JPS President Todd Dixon said his company developed IronGate by addressing the well-chronicled cybersecurity problem for critical infrastructure in a unique manner compared to other firms in the sector.
“Our approach is a little different,” Dixon said during an interview with IWCE’s Urgent Communications. “I would say that 99% of the solutions out there are focused on, ‘How do I find a problem, and how do I deal with it after it’s happened?’ Our solution is intent on stopping the problem from ever happening in the first place. That’s where we separate ourselves from the competition.”
“Essentially, where there are industrial controls—and that can be a water facility, wastewater facility, electric system, dams and any commercial equipment that you don’t want to be hacked—this will help avoid that from happening.”
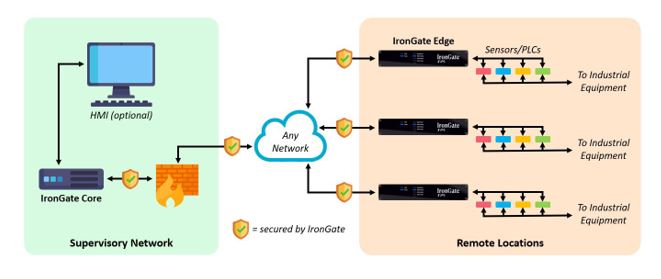
Designed to work with existing supervisory control and data acquisition (SCADA) systems and equipment, IronGate leverages both hardware and software to establish a secure method for the home office of critical-infrastructure entity to communicate with sensors in the field and vice versa (see network diagram above), Dixon said.
In a typical scenario, a JPS Irongate core server would be located at the home office and could be connected to 50 or more IronGate edge devices, each of which would be linked to as many as 100 sensors, according to Dixon.
“The JPS Irongate edge sits out at the site, where the protection is needed,” he said. We put a box in an electric substation, and we connect the items that we don’t want people to [hack] into that box.
“So, what we’re really providing is an absolutely secure connection—between the home office and those sites—that locks the hackers out.”
Dixon said he believe the IronGate approach is superior to the existing technologies employed commonly in the sector.
“Today, people use VPN networks,” Dixon said. “As long as the network is set up perfectly, you’re OK, until someone inside give a key away. If it’s not set up perfectly, once they get into your system, they’re into your entire system—e-mail, finance systems, etc.
“In our cast, even if hackers somehow were able to breach the system, they wouldn’t be able to go past the server at the core. It would never make it back into the regular system.”
At the heart of the IronGate system is a single key that customers will need to guard closely, Dixon said.
“There is a single key that we provide after the system is locked down,” Dixon said. “We ask them to take it and physically put it into a safe.
“For example, if one of our edge units were to fail for whatever reason, they’re going to need to replace it. They will need that [key] to replace it or to make updates. So that, in itself, has its own security to protect the system from people getting into it.”
That applies to all people, including those who work for JPS, Dixon said.
“The other thing that people ask us is, ‘Well, JPS can get into it, right?’ The answer is, ‘No, we can’t,’” Dixon said.
If the key is lost or destroyed, a customer would not have to replace all of its IronGate cores and edge devices, according to Dixon.
“The hardware itself would be good,” he said. “We would just have to come in, reestablish all of the information, recreate the links and set the system up. So, there would be a period where they wouldn’t have our protection.”
IronGate has been beta tested at a major U.S. military facility.
“What we found out was that they had 270 points of contact that were not protected in a way that they should have been, so hackers could get into that,” Dixon said.
“Where we did the beta test, it was one of their newer sites that used a [major carrier’s] secure connection, and we monitored the information coming through. There were attacks that made it through the [carrier] that we stopped.”
In addition, IronGate has been tested in prestigious laboratories.
“We’ve had testing done by four major [entities],” Dixon said. “One is Mandiant FireEye, which was the recommendation from the NSA—they asked us to go to them. They found that the system couldn’t be broken.
“With both [Mandiant] and Cylance [another cybersecurity testing firm], we gave them both hardware and software and asked them to break it. They couldn’t. We even gave them information to help them break it that no one else would have, and they still couldn’t break it.”
Most cybersecurity companies have focused their attention on the lucrative part of the business that tries to protect sensitive documents, but JPS IronGate is designed to secure critical infrastructure that many fear would be prime targets for nation-states to hack as part of larger military attack.
“We’re kind of in a niche market, trying to protect the infrastructure, which we believe is what’s going to be targeted in the next war,” Dixon said. “They’re going to go after these kinds of things to disable you from doing anything … We all know that, without electricity and water, no war is going to go on very long. So, the DoD gets this. They understand that it’s an issue.
“We first thought it would be electrical [plants that would be the primary targets of nation-state attacks during a military conflict]. But after working with the defense agency that we did the beta site with, we found out that wastewater and fresh water is more important. You can store electricity for a while, but you can’t store water that much.”
IronGate’s approach is flexible enough to address the three primary methods that hackers use to attack critical-infrastructure equipment today, Dixon said.
“The worst case would be that you have a system that is not protected at all—which we have seen, in places that kind of scare me, to be honest with you—where the device sitting at a substation of some kind is completely on the open Internet,” Dixon said. “Any hacker can get to that, if they want to, and do whatever they want to it.
“Another is that you have a VPN network that’s established, but it’s not set up properly—it has gaps in the system. That’s a fairly common thing. You think you have everything plugged, and hackers finds their way into the system, plant their [malware] and does their thing. The third would be that you have a good VPN, and it’s fairly well locked down, but you have a rogue employee who hands the keys to someone for some financial gain.
“In all three cases, if you put our device in there, you would stop the hacking of the industrial control.”
JPS expects to begin mass production of IronGate equipment this month, with the core server expected to have a list price of $12,000, while the edge device is expected to cost $13,000, Dixon said. In addition, customers can receive software updates and maintenance services by paying JPS an annual fee that is 17% of the total sales price, he said.
IronGate systems could be used to secure a host of SCADA and IoT-based systems, but Dixon believes it likely will be deployed only in use cases where the risk of being hacked is significant.
“Somewhere, there’s a cutline in all of this process, just based on cost,” Dixon said. “I don’t want to sell something to somebody just to sell it to them. I want it to be a smart sale.”
Dixon acknowledged that developing a cybersecurity solution like IronGate represents a big change for JPS, which has long been recognized as a leader in providing interoperability gateways.
“Quite honestly, it was a tough sell internally, from my point of view,” Dixon said. “[People asked,] ‘Why are you going into cybersecurity? This is a big risk.’ But we know we need to grow, and this is our way to do it.”
Now that IronGate has been developed and is about to hit the market, JPS is faced with the challenge of convincing customers that a company know for enabling interoperable communications also offers a cybersecurity solution that can meet the needs of critical-infrastructure entities.
“That’s the uphill battle we’re fighting, quite honestly,” Dixon said.