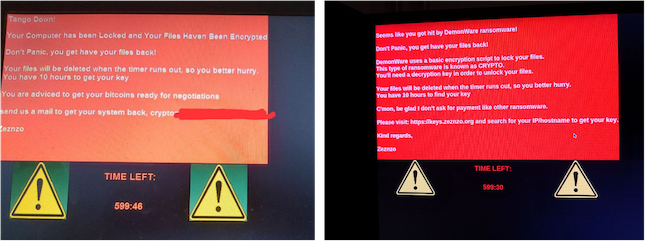
Ransomware attacker offers employees a cut, if they install DemonWare on their organization’s systems
Researchers masqueraded as a rogue employee to engage with a ransomware operator soliciting insiders to plant ransomware on their own organization’s servers in exchange for a portion of the ransom money. Their ploy gave them a front-row seat in a rare ransomware threat — one that comes with a bold social engineering twist.
Crane Hassold, director of threat intelligence for email security firm Abnormal Security, since Aug. 12 has been interacting with the would-be attacker, who he believes is a Nigerian-based business email compromise (BEC) scammer based on the intelligence he has gathered and gleaned from their online interactions.
“It’s an interesting and novel tactic,” says Hassold of the attack.
The scam is somewhat reminiscent of a more targeted ransomware attempt on Tesla last year, when cybercriminals tried to bribe an employee at the carmaker’s Gigafactory in Nevada to the tune of $1 million to help infect the company’s network with ransomware. The employee instead worked with the FBI to help get the cybercriminal, a Russian national, arrested.
Meanwhile, Hassold has been communicating via Telegram with this new extortionist attacker, posing as a willing but nervous employee interested in getting a cut of a potential ransom payment. “I don’t know how successful it will be at the end of the day, but they are not looking at a high success rate. … They want to make enough money to make the ROI.”
The attacker apparently initially attempted to dupe his victims using the usual BEC method of gathering contact information on LinkedIn and sending phishing emails to senior-level executives in hopes of stealing credentials and getting account access. Hassold says when the credential-phishing failed, the attacker pivoted to a ransomware attack deal-making scheme offered via an email message.
“It’s really interesting to me that while we think of ransomware as a technically sophisticated attack, when we think of Nigerian scammers we think of social engineering. Now we have a hybrid attack, using the same social engineering tactics he’s probably using on a daily basis on BEC, credential, and romance scams and tossing it in with ransomware.”
The attack goes like this: The employee receives an email offering $1 million in Bitcoin, or 40% of a $2.5 million ransom bounty, if he or she installs DemonWare ransomware — either physically or remotely — on their company’s Windows server or other computer. If the employee wants to take them up on it, he or she contacts the attacker via their Outlook email address or Telegram account provided in the initial email.
Given that most ransomware attacks begin with a rigged email attachment or via a compromised VPN account or software vulnerability, recruiting an insider to go rogue was an unusual tactic, according to Hassold, especially since it was not a targeted attack.
To read the complete article, visit Dark Reading.